Owning crypto is not the same as owning money in a bank account. There is no central authority, no customer support hotline, and no password reset. Your access to funds depends entirely on you and how you set up your crypto wallet.
The type of wallet, in turn, determines whether you truly control your assets or rely on a third party to hold them for you.
In this article, we’ll explain how crypto wallets work, who really controls your assets, and walk through the main wallet types so you can understand which tools fit your needs.
What is a crypto wallet?
You may be surprised, but a crypto wallet doesn’t store coins in the traditional sense. In reality, it manages the cryptographic keys that prove your ownership of assets recorded on the blockchain. So, the exact definition of the crypto wallet will be a tool that gives you real control over your cryptocurrency.
How does a crypto wallet work? Every wallet works with two core elements. The public address is what you share to receive funds. It functions like a bank account number and is safe to make public. The private key is what gives you authority over those funds. It is the only way to sign transactions and move your assets. Whoever controls the private key controls the money.
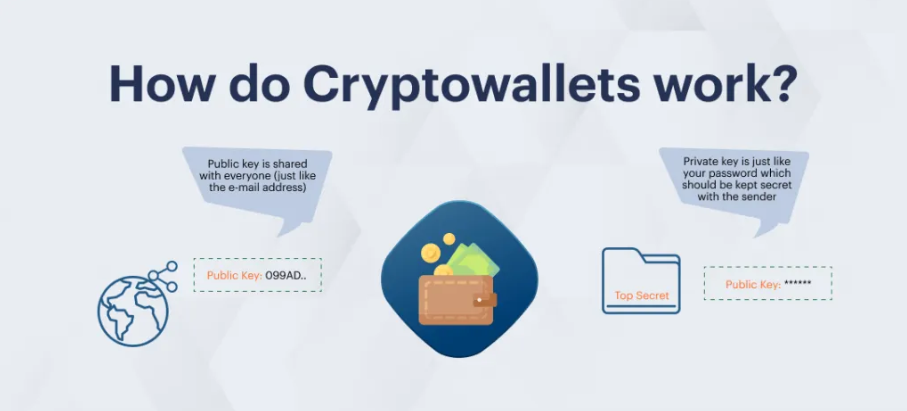
When you send crypto, your wallet uses the private key to create a digital signature. This signature confirms that you approved the transaction without exposing the key itself. The signed transaction is then broadcast to the network and permanently written to the blockchain.
Custodial vs non-custodial wallets
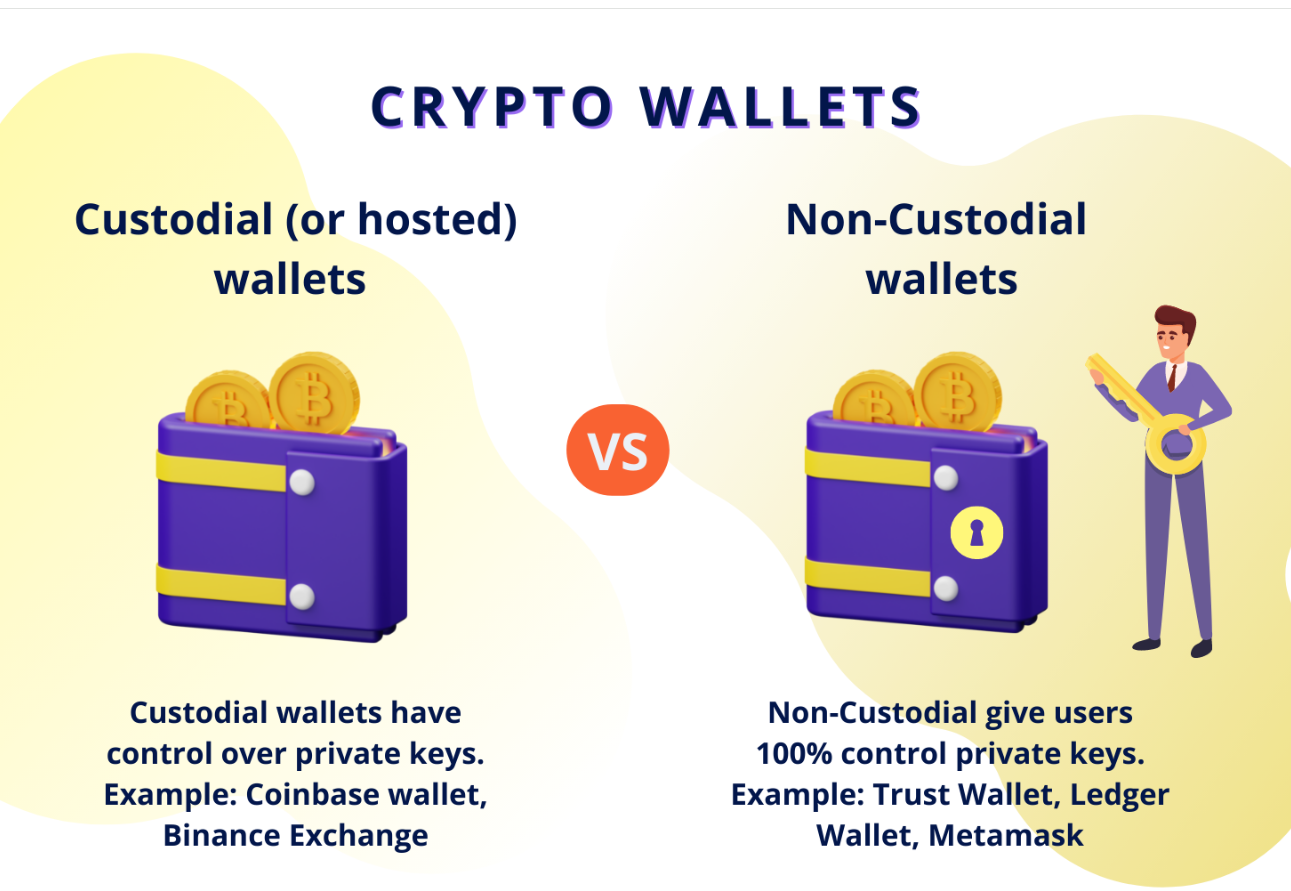
The difference between custodial and non-custodial wallets is simple: who holds the private keys.
To remember the difference, think about the word custodian, someone who is legally responsible for taking care of something that belongs to another person.
In a custodial wallet, the platform acts as the custodian and manages your crypto and private keys for you. When you hold your own keys and control your own funds, you don’t need a custodian, and that’s what a non-custodial wallet is.
Most exchanges and fintech platforms operate like custodians. When you use services like Coinbase or Kraken, you log in with an email and password, and the company signs transactions on your behalf.
In the case of non-custodial wallets, when you hold the private keys yourself, no company can move your funds, freeze your account, or recover access if something goes wrong. Wallets like MetaMask, Ledger, or Trust Wallet give you direct ownership at the protocol level. If the private key or recovery phrase is lost, access is permanently gone.
Custodial wallets reduce friction and provide support, which is useful for onboarding and active trading. Non-custodial wallets remove intermediaries and give you sovereignty over your assets, but demand operational discipline.
Your choice depends on what you value more: ease of use or direct control.
Types of crypto wallets
One crypto wallet can belong to several categories at the same time. It is usually described using two independent dimensions: who controls the private keys and whether the wallet is connected to the internet.
Private key control defines whether a wallet is custodial or non-custodial. The second dimension, internet access, defines whether it is hot or cold.
See the summary table for a clear classification overview.
Note. The Binance exchange wallet (that inside your Binance account) is hot and custodial. Binance Web3 Wallet is hot and non-custodial.
Hot wallets
Hot wallets are connected to the internet. They are built for speed and daily use. Because they are online, they can be targeted by remote attacks: phishing, malware, fake websites, hacked apps, or compromised browser extensions. An attacker doesn’t need physical access; they only need a vulnerability in your device or behavior.
These include software, web, mobile, and desktop wallets.
#1: Software wallets
Examples: MetaMask, Exodus, Atomic Wallet
Software wallets are apps installed on a phone, computer, or browser. They are convenient and usually free, but their safety depends on the security of the device.
If your device is compromised, the wallet can be compromised too, because the attacker may see your screen, steal your keys, or sign transactions.
#2: Web wallets
Examples: Binance Exchange Wallet, Coinbase Exchange Wallet, Blockchain.com Wallet
Web wallets run in a browser or belong to an exchange platform. They are accessible from anywhere, but you fully depend on the provider’s security.
#3: Mobile wallets
Examples: Trust Wallet, Coinbase Wallet, Phantom, Rainbow
Mobile wallets are designed for everyday payments and quick access. They sit between convenience and security and are great for moderate balances.
#4: Desktop wallets
Examples: Exodus Desktop, Electrum, Bitcoin Core
Desktop wallets provide stronger isolation than web wallets while staying relatively easy to use. Their safety depends on keeping the computer updated and free from malware. Remember how often people lose photos or passwords forever just because an old computer died.
Cold wallets
Examples: Ledger, Trezor, SafePal S1
Cold wallets stay offline. Their private keys never touch an internet-connected device, which removes most remote attack vectors. This makes them the standard choice for storing larger amounts over long periods. The trade-off is slower access and less convenience. In this case, the only real risk comes from physical threats.
These include hardware and paper wallets.
#1: Hardware wallets
Examples: Ledger Nano X, Ledger Nano S Plus, Trezor Model T, SafePal S1
They are a form of cold wallet, just a very advanced and practical one. Hardware wallets are physical devices that store private keys offline and sign transactions inside the device. Ledger and Trezor are widely used for this reason.
#2: Paper wallets
Examples: Bitcoin paper wallets generated via bitaddress.org
Paper wallets store keys on physical paper. While they are technically offline, they introduce serious operational risks: loss, damage, theft, and difficult recovery. In modern practice, they are largely outdated and rarely recommended.

Wallet security considerations
Here is a small secret: the quality of a wallet matters a bit less than how it is used. In practice, most crypto losses come from operational mistakes, not from failures in wallet technology.
Phishing is the most common entry point for attackers. They copy the design of real wallets and exchanges and push users to enter recovery phrases or private keys on fake websites.
Note. A legitimate service will never ask for recovery phrases or private keys. Always check URLs carefully and use bookmarks for platforms you trust.
Malware is a major risk because an infected device can log keystrokes, change wallet addresses, or steal sensitive data. A known example is CryptoShuffler, which in 2016 replaced copied Bitcoin addresses in the clipboard and stole at least 23 BTC, about $140,000 at the time, according to BleepingComputer.
Take key management seriously. If your private key or recovery phrase is lost, access is gone permanently. There is no reset button. Store recovery phrases offline, in a physical location that is protected and separate from your device.
Many losses come from simple user error: sending funds to the wrong address, or trusting “support” messages from strangers. Slow down, verify every transaction, and never share wallet credentials.
Security in crypto is behavioral. Being cautious and even a little distrustful are appropriate and healthy traits here.
How to choose the right crypto wallet
Choosing a wallet relies on how you actually use crypto.
If you are just starting out or value simplicity, a custodial wallet on an exchange or a well-designed mobile app is the most practical entry point. For example, Binance Wallet or Phantom.
For active trading, hot wallets and web wallets are built for speed. They make frequent transactions efficient and reduce friction when interacting with exchanges or DeFi platforms.
For long-term storage, hardware wallets are the industry standard. They isolate private keys from online environments and drastically reduce attack surface.
If you want full ownership without buying dedicated hardware, non-custodial mobile or desktop wallets are a practical middle ground. They let you control your private keys while still being easy to access and use for everyday transactions.
Conclusion
Let’s summarize the difference between the main crypto wallet types. Making a choice between “hot wallet vs cold wallet” is about balancing convenience and security. Hot wallets give you speed and flexibility for daily use, while cold wallets prioritize long-term protection.
In the battle “custodial vs. non-custodial wallet”, the question is responsibility. Custodial wallets trade control for simplicity and support. Non-custodial wallets give you full ownership but require careful key management and strong security habits.
There is no universally “best” wallet. You should ask yourself a few practical questions: how much value you are securing, how often you move funds, and how comfortable you are managing your own security.

Disclaimer: All materials on this site are for informational purposes only. None of the material should be interpreted as investment advice. Please note that despite the nature of much of the material created and hosted on this website, HODL FM is not a financial reference resource, and the opinions of authors and other contributors are their own and should not be taken as financial advice. If you require advice, HODL FM strongly recommends contacting a qualified industry professional.





